Part of practicing "assume breach" security is by implementing Chaos Engineering.
In the event your organization suffers a breach its important to be prepared to for it and have the controls in place to mitigate it.
Not only should you have controls but you should regularly test this controls. A good way to automate this is by using Chaos Security Engineering.
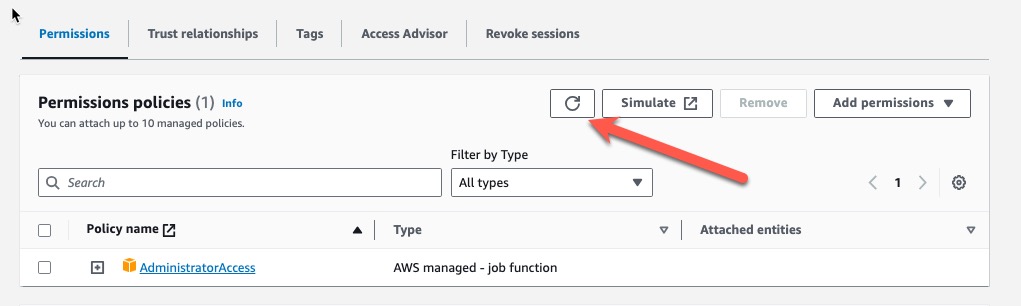
Lets take a look at the following scenario, an organization has a control which states the AWS Managed Policy: AdministratorAccess shall not be used.
When you launch the CloudFormation stack included in this repo, it will respond in two cases:
- A new role created with the AdministratorAccess policy
- The AdministratorAccess policy attached to an existing role
To verify this create a role and attach the AdministratorAccess policy. You will see something like this:
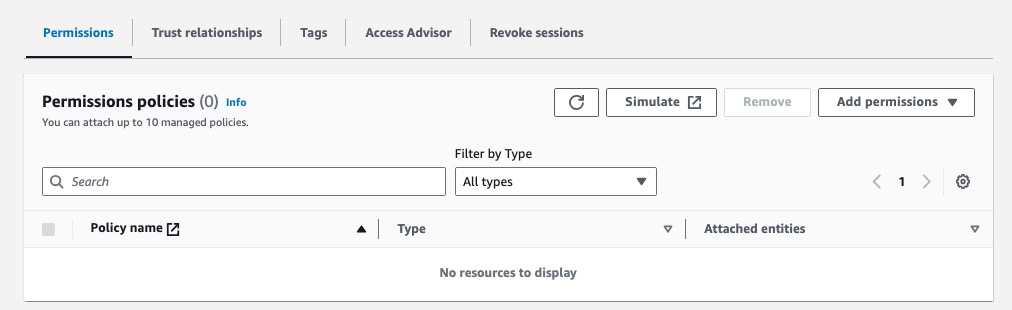
Wait a few seconds, then refresh, you will see the policy was automatically removed. Now, try attaching it to the the role (case #2), again its automatically removed.
Organizaitions often have hundreds of controls so manually testing them all on a regular basis would not be practical. This is where Chaos Security Engineering (CSE) comes in. You can create different "experiments" to test or simillate breaches and security violations and see how your system responds.
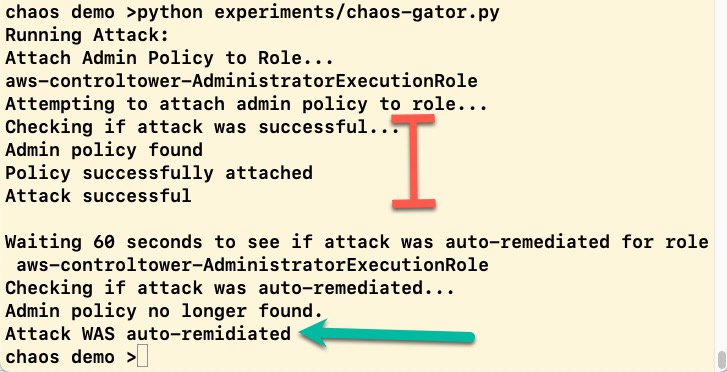
In the experiments folder of this repo you will see a script called "chaos-gator.py". This script performs the following CSE experiment:
- Looks for a role which doesn't have the AdministratorAccess policy attached
- Try to attach the role, if it can't it will keep trying other roles
- If it can attach the policy, it then checks to see if the policy was automatically removed
Here is a sample run:
Taking this example further you can add reporting to your SOC team, for example automatically posting to a Slack channel that adding the AdministratorAccess policy was attempted. You could also turn off autoremediation and see how long it takes the SOC team to detect (MTTD) and remediate it (MTTR).
What other experiements can you think of?